October 2004
1. Given a list of marks ranging from 0 to 100. Write a C# program to compute and print number of students who have obtained marks
1)in the range 81 to 100
2)in the range 61 to 80
3)in the range 41 to 60
4)in the range 0 to 40.
using System;
class Demo
{
public static void Main(string[] args)
{
int dis=0, I=0, II=0, fail=0;
for(int x=0; x<args.Length; x++)
if (int.Parse(args[x]) > 80)
++dis;
else if (int.Parse(args[x]) > 60 )
++I;
else if (int.Parse(args[x]) > 40 )
++II;
else
++fail;
Console.WriteLine ("\nNumber of students in the range 81 to 100 - " + dis);
Console.WriteLine ("\nNumber of students in the range 61 to 80 - " + I);
Console.WriteLine ("\nNumber of students in the range 41 to 60 - " + II);
Console.WriteLine ("\nNumber of students in the range 0 to 40 - " + fail);
}
}
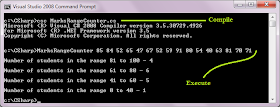 |
| Output (Passing Arguments through command line) |
2. Write a method Prime that returns true if argument is a prime number and returns false otherwise?
using System;
public class Demo
{
public static bool Prime(int num)
{
for (int i=2; i<num; i++)
if (num % i == 0)
return false;
return true;
}
public static void Main()
{
Console.WriteLine ("Enter a number - ");
int x = int.Parse (Console.ReadLine());
if (Prime(x))
Console.WriteLine (x + " is a prime number.");
else
Console.WriteLine (x + " is not a prime number.");
}
}
3. Define an interface power that contains three methods viz.
i) to calculate the square of the given number
ii) to calculate cube of the given number
iii) to calculate power of 'm' raised to 'n'
Define a class demo which implements this interface.
Write a main method to check your code?
using System;
interface Power
{
int square (int m);
int cube (int m);
int pwr (int m, int n);
}
class Demo : Power
{
public int square (int m)
{
return m*m;
}
public int cube (int m)
{
return m*m*m;
}
public int pwr (int m, int n)
{
int r=m;
if (n!=0)
{
for (int i=1; i<n; i++)
m*=r;
return m;
}
else
return 0;
}
}
class Test
{
public static void Main()
{
Console.Write ("Enter a number - ");
int num = int.Parse(Console.ReadLine());
Console.Write ("Enter the power value - ");
int x = int.Parse(Console.ReadLine());
Demo obj = new Demo();
Console.WriteLine("Square of " + num + " is - " + obj.square(num));
Console.WriteLine("Cube of " + num + " is - " + obj.cube(num));
Console.WriteLine(num + "^" + x + " is - " + obj.pwr(num,x));
}
}
4. Write a program that will take 10 integer numbers from command line and then print all the numbers divisible by 5 and 7. Also print sum of all those numbers?
using System;
class Demo
{
public static void Main(String[] arg)
{
int sum = 0;
Console.WriteLine ("\nNumbers divisible by 5 or 7 -");
for (int i=0; i<arg.Length; i++)
if ((int.Parse(arg[i]) % 5 == 0) || (int.Parse(arg[i]) % 7 == 0))
{
Console.WriteLine (arg[i]);
sum+=int.Parse(arg[i]);
}
Console.WriteLine ("\n\nSum = " + sum);
}
}
5. Write a Program that will read the value of 'x' and evaluate the value of 'y' as follows.
y=1 for x>0
y=0 for x=0
y=-1 for x<0
using else if statement?
using System;
class Demo
{
public static void Main()
{
int x;
Console.Write ("\nEnter the value of x -");
x = int.Parse(Console.ReadLine());
if (x>0)
Console.WriteLine("y = 1");
else if (x==0)
Console.WriteLine("y = 0");
else if (x<0)
Console.WriteLine("y = -1");
}
}
6. Write a program to convert the given temperature in Fahrenheit to Celsius.
[Formula: C = (F-32)/1.8]
using System;
class Demo
{
public static void Main()
{
Console.Write("Enter the Fahrenheit Value - ");
double F = double.Parse(Console.ReadLine());
double C = (F-32)/1.8;
Console.WriteLine("Celsius - " + C);
}
}
7. Write a class Date that includes data member day, month and year and methods that could implement the following tasks.
i)Read a date from Keyboard
ii)DisplayDate a Date
iii)Increment a date by one day
iv)Compare two dates to see which is greater.
using System;
class Date
{
private int day;
private int month;
private int year;
public void ReadDate()
{
Console.WriteLine (" *** Enter the Date ***");
Console.Write("Day - ");
day = int.Parse(Console.ReadLine());
Console.Write("Month - ");
month = int.Parse(Console.ReadLine());
Console.Write("Year - ");
year = int.Parse(Console.ReadLine());
}
public void DisplayDate()
{
Console.WriteLine(day + "-" + month + "-" + year);
}
public static void Compare(Date d1, Date d2)
{
if (d1.year>d2.year)
{
Console.WriteLine("Greater Date is - ");
d2.DisplayDate();
}
else if (d1.year==d2.year)
{
if (d1.month>d2.month)
{
Console.WriteLine("Greater Date is - ");
d2.DisplayDate();
}
else if (d1.month == d2.month)
{
if (d1.day>d2.day)
{
Console.WriteLine("Greater Date is - ");
d2.DisplayDate();
}
else if (d1.day == d2.day)
Console.WriteLine("Both the dates are equal.");
else
{
Console.WriteLine("Greater Date is - ");
d1.DisplayDate();
}
}
else
{
Console.WriteLine("Greater Date is - ");
d1.DisplayDate();
}
}
else
{
Console.WriteLine("Greater Date is - " );
d1.DisplayDate();
}
}
public static void Incr(Date d1)
{
d1.day++;
if (d1.day==29)
{
if (d1.month==2)
{
if (d1.year%4 != 0 && d1.year%100 !=0)
{
d1.day=1;
d1.month++;
}
}
}
else if (d1.day==30)
{
if (d1.month==2)
{
if (d1.year%4 == 0 && d1.year%100 ==0)
{
d1.day=1;
d1.month++;
}
}
}
else if (d1.day==31)
{
if(d1.month==2 || d1.month==4 || d1.month==6 || d1.month==9 || d1.month==11)
{
d1.day=1;
d1.month++;
}
}
else if (d1.day==32)
{
d1.day=1;
d1.month++;
if(d1.month==13)
{
d1.month=1;
d1.year++;
}
}
}
}
class Test
{
public static void Main()
{
Date d1 = new Date();
Console.WriteLine("Enter 1st Date - \n");
d1.ReadDate();
d1.DisplayDate();
Date d2 = new Date();
Console.WriteLine("\n\nEnter 2nd Date - \n");
d2.ReadDate();
d2.DisplayDate();
Console.WriteLine ("\nResult - \n");
Date.Compare(d1,d2);
Console.Write("\n\nIncrementing 1st date by 1 day - ");
Date.Incr(d1);
d1.DisplayDate();
Console.Write("\n\nIncrementing 2nd date by 1 day - ");
Date.Incr(d2);
d2.DisplayDate();
}
}
April 2005
8. Write a program that prints the following format.
#####
####
###
##
#
using System;
class Style
{
public static void Main()
{
for(int i=0; i<5; i++)
{
for(int s=0; s<i;s++)
{
Console.Write(" ");
}
for(int j=5; j>i; j--)
{
Console.Write("#");
}
Console.WriteLine();
}
}
}
9. Write a program to convert the temperature in Fahrenheit (starting from 98.5 to 102 in steps of 0.1) to Celsius using the formula C = (F-32)/1.8 and display the values in tabular form?
using System;
class Style
{
public static void Main()
{
Console.WriteLine("Fahrenheit ---- Celsius");
for(double F=98.5; F<=102; F=F+0.1)
{
Console.WriteLine("{0:F1} -------- {1:F2}" , F, ((F-32)/1.8));
}
}
}
10. Write a program to print the following Floyd's triangle.
1
2 3
4 5 6
7 8 9 10
............
..............
79..............91
using System;
class Floyd
{
public static void Main()
{
int c=1;
for(int i = 0; i<14; i++)
{
for(int j=0; j<i; j++)
{
Console.Write(c+ " ");
c++;
}
Console.WriteLine();
}
}
}
October 2005
11. Write a program to print the following output.
1
2 2
3 3 3
4 4 4 4
5 5 5 5 5
using System;
class Demo
{
public static void Main()
{
for(int i=1; i<=5; i++)
{
for(int s=5; s>i; s--) //loop for space
Console.Write(" ");
for(int j=1; j<=i; j++)
Console.Write(i + " ");
Console.WriteLine();
}
}
}
12. Develop a program that prompts the user to input name, door number, street, city and pincode and stores them in the address record designed as a structure and display them in appropriate manner.
using System;
struct Address
{
public string name, door_number, street, city, pincode;
}
class Demo
{
public static void Main()
{
Address adr;
Console.WriteLine("### Enter your details ###\n");
Console.Write("Name - ");
adr.name = Console.ReadLine();
Console.Write("Door Number - ");
adr.door_number = Console.ReadLine();
Console.Write("Street - ");
adr.street = Console.ReadLine();
Console.Write("City - ");
adr.city = Console.ReadLine();
Console.Write("Pincode - ");
adr.pincode = Console.ReadLine();
Console.WriteLine("\n\n### Your Address is ###\n");
Console.WriteLine(adr.name);
Console.WriteLine(adr.door_number +", " + adr.street + ", ");
Console.WriteLine(adr.city + "-" + adr.pincode);
}
}
13. Write a program to print the following Pascal's triangle.
Hint: If we denote the rows by i and the columns by j, then any element (except the boundary elements) in the triangle is given by P[ij] = P[i-1,j-1] + p[i-1,j]?
1
1 1
1 2 1
1 3 3 1
1 4 6 4 1
1 5 10 10 5 1
using System;
class Demo
{
public static void Main()
{
int n, i, j, c;
Console.Write("Enter an integer bound > ");
n = Convert.ToInt32(Console.ReadLine());
for (i = 0; i < n; i++)
{
c = 1;
for (j = 0; j <= i; j++)
{
Console.Write(c + " ");
c = (c * (i - j)) / (j + 1);
}
Console.WriteLine();
}
}
}
14. Write a program that accepts two double type numbers from the user and display addition, subtraction, multiplication, division and modulous of those two numbers?
using System;
class Demo
{
public static void Main()
{
double a,b;
Console.Write("Enter num 1 - ");
a = double.Parse(Console.ReadLine());
Console.Write("Enter num 2 - ");
b = double.Parse(Console.ReadLine());
Console.WriteLine("\nAddition = {0:f2}", (a+b));
Console.WriteLine("Subtraction = {0:f2}", (a-b));
Console.WriteLine("Multiplication = {0:f2}", (a*b));
Console.WriteLine("Division = {0:f2}", (a/b));
Console.WriteLine("Modulous = {0:f2}", (a%b));
}
}
15. Write a program to add and subtract two complex numbers using operator overloading.
using System;
class Complex
{
private int rel;
private int img;
public Complex()
{
rel=0;
img=0;
}
public Complex(int r, int i)
{
rel = r;
img = i;
}
public void show()
{
Console.WriteLine(rel + " + " + img + "i");
}
public static Complex operator + (Complex c1, Complex c2)
{
Complex c3 = new Complex();
c3.rel = c1.rel + c2.rel;
c3.img = c1.img + c2.img;
return c3;
}
public static Complex operator - (Complex c1, Complex c2)
{
Complex c3 = new Complex();
c3.rel = c1.rel - c2.rel;
c3.img = c1.img - c2.img;
return c3;
}
}
class Demo
{
public static void Main()
{
Complex c1 = new Complex(2,3);
c1.show();
Complex c2 = new Complex(4,4);
c2.show();
Complex c3 = c1 + c2;
Console.WriteLine("-------------------------------");
Console.Write("\nAddition (c1 + c2) = ");
c3.show();
c3 = c2 - c1;
Console.Write("\nSubtraction (c2 - c1) = ");
c3.show();
}
}
April 2006
16. Create class named Double. This class contains three double numbers. Overload +,-,*, / operators so that they can be applied to the objects of class Double. Write a C# program to test it?
using System;
class Double
{
double x, y, z;
public Double()
{
x=0;
y=0;
z=0;
}
public Double(double a, double b, double c)
{
x=a;
y=b;
z=c;
}
public void show()
{
Console.WriteLine("x = {0:F2}", +x);
Console.WriteLine("y = {0:F2}", +y);
Console.WriteLine("x = {0:F2}", +z);
}
public static Double operator + (Double d1, Double d2)
{
Double d3 = new Double();
d3.x = d1.x + d2.x;
d3.y = d1.y + d2.y;
d3.z = d1.z + d2.z;
return d3;
}
public static Double operator - (Double d1, Double d2)
{
Double d3 = new Double();
d3.x = d1.x - d2.x;
d3.y = d1.y - d2.y;
d3.z = d1.z - d2.z;
return d3;
}
public static Double operator * (Double d1, Double d2)
{
Double d3 = new Double();
d3.x = d1.x * d2.x;
d3.y = d1.y * d2.y;
d3.z = d1.z * d2.z;
return d3;
}
public static Double operator / (Double d1, Double d2)
{
Double d3 = new Double();
d3.x = d1.x / d2.x;
d3.y = d1.y / d2.y;
d3.z = d1.z / d2.z;
return d3;
}
}
class Demo
{
public static void Main()
{
Double d1 = new Double(10.095,12.93,14.982);
Double d2 = new Double(23.893,24.84,23.940);
Console.WriteLine("d1 ##### ");
d1.show();
Console.WriteLine("\nd2 ##### ");
d2.show();
Double d3 = new Double();
d3 = d1+d2;
Console.WriteLine("\nd1+d2 ##### ");
d3.show();
d3 = d2-d1;
Console.WriteLine("\nd2-d1 ##### ");
d3.show();
d3 = d2*d1;
Console.WriteLine("\nd2*d1 ##### ");
d3.show();
d3 = d2/d1;
Console.WriteLine("\nd2/d1 ##### ");
d3.show();
}
}
17. Write a void type method that takes two integer type value parameters and one integer type out parameter and returns the product of two parameters through the out parameter. Write a C# program to test it's working?
using System;
class Demo
{
public static void Product(int a, int b, out int c)
{
c = a*b;
}
public static void Main()
{
int res;
Product(10,20,out res);
Console.WriteLine("10 * 20 = " +res);
}
}
18. Create a class Example to hold one integer value. Include a constructor to display a message "Object is created." and a destructor to display a message "Object is destroyed." Write a C# program to demonstrate the creation and destruction of objects of example class?
using System;
class Example
{
private int i;
public Example()
{
i=0;
Console.WriteLine("Object is created.");
}
~Example()
{
Console.WriteLine("Object is destroyed.");
}
}
class Demo
{
public static void Main()
{
Example e = new Example();
}
}
19. Write your own Exception NumberNotInRange. Write a C# program that throws NumberNotInRange exception if number entered by user is not in the range 1 to 100?
using System;
class NumberNotInRange : Exception
{
public NumberNotInRange()
{
Console.WriteLine("The number should be between 1 to 100.");
}
}
class Demo
{
public static void Main()
{
try
{
Console.Write("Enter a number - ");
int i = int.Parse(Console.ReadLine());
if(i<1 || i>100) throw new NumberNotInRange();
}
catch(Exception e)
{
Console.WriteLine(e);
}
}
}
October 2006
20. Write a program to print the following output.
*******
*** ***
** **
* *
using System;
class Demo
{
public static void Main()
{
for(int a=0; a<7; a++)
Console.Write("*");
Console.WriteLine();
for(int i=0; i<3; i++)
{
for(int j=3; j>i; j--)
{
Console.Write("*");
}
for(int s=0; s<=2*i; s++)
Console.Write(" ");
for(int k=3; k>i; k--)
Console.Write("*");
Console.WriteLine();
}
}
}
21. Write a method Maximum() that takes an array as an input parameter and returns maximum and minimum values to Main(). Write a complete c# program to test the above method?
using System;
class Demo
{
public static void Maximum(out int min, out int max, params int[] a)
{
Array.Sort(a);
min = a[0];
max = a[a.Length-1];
}
public static void Main()
{
int[] a = {10,22,23,14,5};
int min, max;
Maximum(out min, out max, a);
Console.WriteLine("Minimum - " + min);
Console.WriteLine("Maximum - " + max);
}
}
22. Define a Time class containing following members.
-Two integer data members minutes and hours.
-Two overloaded constructors.
-One method to display the class data members.
One of the constructor takes two integer parameters to assign value to two data members and other constructor takes one integer parameter representing total number of minutes and converts it into hours and minutes. Write a complete program to verify the operation ofconstructor and the method?
using System;
class Time
{
int mm, hh;
public Time(int mins, int hrs)
{
mm = mins;
hh = hrs;
}
public Time(int tmins)
{
mm = tmins%60;
hh = tmins/60;
}
public void display()
{
Console.WriteLine ("The time is - " + hh + ":" + mm);
}
}
public class Demo
{
public static void Main()
{
Time t1 = new Time(44, 1);
Time t2 = new Time(100);
t1.display();
t2.display();
}
}
April 2007
23. Write a program that will read the name from the keyboard an display it on the screen. The program should throw an exception when the length of the name is more than 15 characters. Design your own exception?
using System;
class InvalidName : Exception
{
public InvalidName()
{
Console.WriteLine("Invalid Name Length : The name should not be more than 15 characters in length.");
}
}
class Demo
{
public static void Main()
{
try
{
Console.WriteLine("Enter your name - ");
string nm = Console.ReadLine();
if(nm.Length>15) throw new InvalidName();
Console.WriteLine("Your Name is - "+nm);
}
catch(Exception e)
{
Console.WriteLine(e);
}
}
}
24. Write a program to generate following triangle.
1
2 3 2
3 4 5 4 3
4 5 6 7 6 5 4
5 6 7 8 9 8 7 6 5
using System;
class Demo
{
public static void Main()
{
int count;
for(int i=1; i<=5; i++)
{
count = i;
for (int j=0; j=i ; k++)
{
Console.Write(count + " ");
count --;
}
Console.WriteLine();
}
}
}
25. Write a method that computes the sum of digits of a given integer number. Write a program to test the above method?
using System;
class Number
{
public int Sum(int num)
{
int n = num;
int sum = 0;
while(num>1)
{
n = num%10;
num = num / 10;
sum = sum + n;
}
return sum;
}
}
class Demo
{
public static void Main()
{
Number obj = new Number();
Console.Write("Enter a number - ");
int a = int.Parse(Console.ReadLine());
Console.WriteLine("\n Sum of Digits is - " + obj.Sum(a));
}
}
26. Given are two 1 dimensional arrays which are in sorted order. Write a program to merge them into a simple sorted array 'C' that contains every item from array 'A' and 'B' in ascending order?
using System;
class Demo
{
public static void Main()
{
int[] A = {1,3,5,7,9};
int[] B = {0,2,4,6};
int[] C = new int[A.Length+B.Length];
for(int i=0; i<A.Length; i++)
C[i] = A[i];
for(int i=A.Length, j=0; j<B.Length; i++, j++)
C[i] = B[j];
Console.WriteLine("\nElements of Array C Before Sorting - ");
foreach(int a in C)
{
Console.Write(a + " ");
}
for(int i=0; i<C.Length; i++)
{
for(int j=0; j<C.Length; j++)
{
if(C[i]<C[j])
{
int temp = C[i];
C[i] = C[j];
C[j] = temp;
}
}
}
Console.WriteLine("\n\nElements of Array C After Sorting - ");
foreach(int a in C)
{
Console.Write(a + " ");
}
}
}
27. Write a program to overload binary ‘*’ and unary ‘-‘ for the class having three integer data members.
using System;
class Dimension
{
private int x, y, z;
public Dimension(int x1, int y1, int z1)
{
x=x1;
y=y1;
z=z1;
}
public static Dimension operator * (Dimension d1,Dimension d2)
{
Dimension d3 = new Dimension(0,0,0);
d3.x = d1.x * d2.x;
d3.y = d1.y * d2.y;
d3.z = d1.z * d2.z;
return d3;
}
public static Dimension operator - (Dimension dim)
{
dim.x = -dim.x;
dim.y = -dim.y;
dim.z = -dim.z;
return dim;
}
public void display()
{
Console.WriteLine ("x = " + x + ", y= " + y + ", z = " + z);
}
}
public class Test
{
public static void Main()
{
Dimension dim1 = new Dimension(1,2,3);
Dimension dim2 = new Dimension(10,20,30);
Console.WriteLine ("\nDimension dim1 - ");
dim1.display();
Console.WriteLine ("\nDimension dim2 - ");
dim2.display();
Dimension dim3 = dim1*dim2;
Console.WriteLine ("\ndim1 * dim2 = ");
dim3.display();
Console.WriteLine ("\n-dim3 = ");
dim3=-dim3;
dim3.display();
}
}
28. Create a class named Integer to hold two integer values. Design a method Swap that could take two Integer objects as parameters and swap their contents. Write a Main program to implement class Integer and method Swap?
using System;
class Integer
{
int x, y;
public Integer()
{
x=0;
y=0;
}
public Integer(int a, int b)
{
x=a;
y=b;
}
public static void Swap(ref Integer I1, ref Integer I2)
{
Integer temp = new Integer();
temp.x = I1.x;
I1.x = I2.x;
I2.x = temp.x;
temp.y = I1.y;
I1.y = I2.y;
I2.y = temp.y;
}
public void show()
{
Console.WriteLine("x = " + x);
Console.WriteLine("y = " + y);
}
}
class Demo
{
public static void Main()
{
Integer I1 = new Integer(2,4);
Integer I2 = new Integer(1,3);
Console.WriteLine("\n ----- Before Swapping ----- ");
Console.WriteLine("I1 - ");
I1.show();
Console.WriteLine("\nI2 - ");
I2.show();
Integer.Swap(ref I1, ref I2);
Console.WriteLine("\n ----- After Swapping ----- ");
Console.WriteLine("I1 - ");
I1.show();
Console.WriteLine("\nI2 - ");
I2.show();
}
}
29. Define a exception called "NoMatchException" that is thrown when a string is not equal to "TYBSCIT". Write a program tht uses this exception?
using System;
class NoMatchException : Exception
{
public NoMatchException()
{
Console.WriteLine("Error : String not matched.");
}
}
class Demo
{
public static void Main()
{
try
{
Console.Write("Enter a message - ");
string msg = Console.ReadLine();
if (msg!="TYBSCIT") throw new NoMatchException();
}
catch (Exception e)
{
Console.WriteLine(e);
}
}
}
April 2008
30. Write a program to create a class called ‘Point’ that has two integer member variables to represent the x and y coordinates of a point. Include as operator method for unary operator ‘++’ to increment a Point object?
using System;
class Point
{
private int x;
private int y;
public Point (int x1, int y1)
{
x=x1;
y=y1;
}
public void show()
{
Console.WriteLine ("x = " + x + " ,y = " + y);
}
public static Point operator ++ (Point p)
{
p.x = ++p.x;
p.y = ++p.y;
return p;
}
}
class Test
{
public static void Main()
{
Point pt = new Point (3,6);
Console.Write("The co-ordinates of point pt is ");
pt.show();
pt++;
Console.Write("The co-ordinates of point pt after pt++ is ");
pt.show();
}
}
31. A bank charges commission on the issue of Demand Drafts at the following rates.
DD Amount Commission
Upto Rs. 500 Rs. 10
Rs. 501 to Rs. 1000 Rs. 15
Rs. 1001 to Rs. 5000 Rs. 25
Rs. 5001 to Rs. 10000 Rs. 30
Above Rs. 10000 Rs. 3 for every Rs. 1000
Write a program which accepts DD amount from the terminal and calculate the commission payable and print it along with the DD amount?
using System;
class Bank
{
public static void Main()
{
Console.Write("Enter DD Amount - ");
double amt = double.Parse(Console.ReadLine());
double comm;
if(amt<=500)
comm=10;
else if(amt<=1000)
comm=15;
else if(amt<=5000)
comm=25;
else if(amt<=1000)
comm=30;
else
comm = (amt/1000)*3;
Console.WriteLine("\nAmount - {0:F2}", amt);
Console.WriteLine("Commission - {0:F2}", comm);
Console.WriteLine("Total - {0:F2}", (amt+comm));
}
}
32. Write a program to create a class named AudioVideoRecord that store name of the movie, year of it's release and it's price. From this another class named SongRecord, which has a member variable for storing number of songs. Both of these classes should include appropriate constructors for the initialization of their data members and a display() method to display their data members. Test the above classes by creating object of SongRecord in Main() method?
using System;
class AudioVideoRecord
{
private string name, year, price;
public AudioVideoRecord(string nm, string yr, string pr)
{
name = nm;
year = yr;
price = pr;
}
public void display()
{
Console.WriteLine ("Name - " + name);
Console.WriteLine ("Year - " + year );
Console.WriteLine ("Price - " + price );
}
}
class SongRecord : AudioVideoRecord
{
private string NumberOfSongs;
public SongRecord(string nm, string yr, string pr, string nos) : base (nm,yr,pr)
{
NumberOfSongs = nos;
}
public new void display()
{
base.display();
Console.WriteLine ("Number of Songs - " + NumberOfSongs );
}
}
class Test
{
public static void Main()
{
SongRecord obj = new SongRecord("MNIK", "2010", "150", "4");
obj.display();
}
}
33. Write a program that declares a interface with a method definition calculating the average of n numbers. Implement this interface in a class called Vehicleavg to calculate the average mileage of vehicles. Test the above class by calling average method inside Main()?
using System;
interface Avg
{
int average(params int[] a);
}
class Vehicleavg : Avg
{
public int average(params int[] a)
{
int sum=0;
for (int i=0; i<a.Length; sum+=a[i], i++);
return (sum/a.Length);
}
}
class Test
{
public static void Main()
{
Vehicleavg obj = new Vehicleavg();
Console.WriteLine("Average is - " +obj.average(23,14,56,45,34,78,63,67,29,34));
}
}
April 2009
34. Write a program that swaps any two rows of a 3 x 3 matrix. The matrix must be implemented as a two dimensional array. Accept row numbers of the rows to be swapped from the user?
using System;
class Matrix
{
int[,] m;
public Matrix()
{
m = new int[3,3];
}
public void store()
{
for (int i=0; i<3; i++)
for (int j=0; j<3; j++)
m[i,j] = int.Parse( Console.ReadLine());
}
public void show()
{
for (int i=0; i<3; i++)
{
for (int j=0; j<3; j++)
Console.Write (m[i,j] + " ");
Console.WriteLine();
}
}
public void swap(int Row1, int Row2)
{
int[] x = new int[3];
for (int j=0; j<3; j++)
{
x[j] = m[Row1,j];
m[Row1, j] = m[Row2, j];
m[Row2, j] = x[j];
}
}
}
class Test
{
public static void Main()
{
Matrix objM = new Matrix();
Console.WriteLine ("Enter array elements - ");
objM.store();
Console.WriteLine ("The array is - ");
objM.show();
Console.Write("Enter rows to be swapped - ");
int r1 = int.Parse(Console.ReadLine());
int r2 = int.Parse(Console.ReadLine());
objM.swap(--r1,--r2);
Console.WriteLine("\nArray after swapping of rows - ");
objM.show();
}
}
35. Define a class Kilometer with a double data member distance and a constructor to initialize it. Include operator methods such that you will be able to perform the following operations.
If ((new Kilometer(22)*3)>new Kilometer(145))
System.Console.WriteLine(“ 22 * 3 ”);
else
System.Console.WriteLine(“ 145 “);?
using System;
class Kilometer
{
double distance;
public Kilometer(double d)
{
distance = d;
}
public static Kilometer operator * (Kilometer k, double d)
{
k.distance *= d;
return k;
}
public static bool operator > (Kilometer k1, Kilometer k2)
{
if (k1.distance>k2.distance)
return true;
else
return false;
}
public static bool operator < (Kilometer k1, Kilometer k2)
{
if (k1.distance<k2.distance)
return true;
else
return false;
}
}
class test
{
public static void Main()
{
if ( (new Kilometer(22)*3) > new Kilometer(145) )
Console.WriteLine ("22 * 3");
else
Console.WriteLine (" 145 ");
}
}
























